In this two part series I take a look at the start of a new investigation hurdle in mobile forensics; a device running KaiOS. The first part will simply introduce the group to a minuscule amount of KaiOS history and architecture and extraction and the second part to the parsing and decoding. So, let’s get started!
It was not long ago I was dealing with the burners of old like the Kyocera SE47 and KE413, Sanyo SCP-4920, Motorola T720 and V120x, and Nokia’s 3570, 6370 along with many others I am sure you can resurrect from your memory. The connection to these devices and the lack of support from the few vendors often left one simply photographing the screen or manually digging through the data (if you were lucky enough to obtain it). If you remember BitPim and traversing the filesystem manually a big high five; and a big bonus if you know what I am talking about when I say BREW and not think of your favorite IPA, pale, or stout. If you did think of a nice beer, jump online and pick up my book Mobile Forensic Investigations where I talk bout that pesky operating system of old. Very few devices are still around running this type of OS and most investigations simply deal with Android or iOS so you can give a big sigh of relief, but the burner of today is just as tricky.
Today’s examiners now have to deal with KaiOS and the devices that are running this Boot to Gecko OS (B2G OS). This operating system is open source and a fork of Firefox OS, and as we dive deeper into the data on these devices you will see why this operating system can be referred to as a web-based mobile OS. KaiOS was originally developed in 2017 to give feature phones (non-touch) a way to give a smartphone look to a feature phone, bringing the smart feature phone to life. Google owns much of the US based company as does Reliance Jio who sells more devices world wide running this OS. Built with access to the KaiStore, users can download and use apps that are built specifically to run on the operating system. More and more apps become available daily adding another level to the investigation of these devices as currently most companies in the forensic industry do not support the parsing of third-party apps from this OS. Investigators should be prepared to deal with these devices as their popularity and low cost drive a new industry around the world with over 30 million phones using KaiOS.
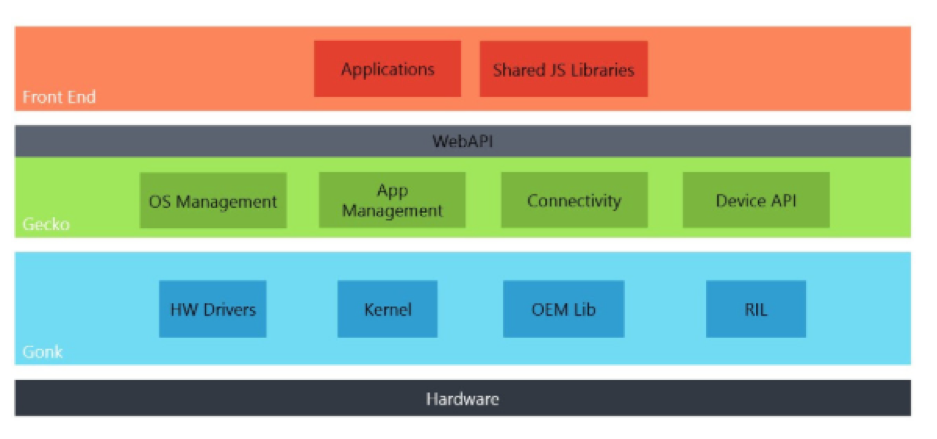
The technical aspects and operating system in a nutshell must be mentioned if not for the fantastic names given to the various levels of the operating system. At the lowest level lives Gonk where the Linux kernel and associated members thrive and drive the KaiOS stack as the interface between Gecko and hardware. It is Gonk that controls the hardware and is the gatekeeper of this level. Gecko is the KaiOS runtime and is the engine that renders/controls/operates the HTML to hardware as the interface between the content (web) and the device. It is here that the parsing and rendering of HTML5 is provided and the API are exposed to communicate to the functions of the hardware. The final or front end of the KaiOS device is what the user interacts with and this is Gaia. Anything that the user sees on the device is the Gaia layer and uses HTML, CSS, and JavaScript. This layer is a basic layer with operation using the mentioned web protocols but also can interact with the device hardware using several available APIs. For any Greek mythology buffs you might be interested in Gaia and the name origins.
In simple terms KaiOS is a transactional and active web connection and rendering interface with an extremely small footprint taking up little power and storage. This gives manufacturers flexibility in the form factor for their produced devices and honestly the ability to produce an internet ready device for an extremely low price bringing in a completely new vertical– customers that either cannot afford a traditional smartphone or want a throw away device (AKA burner).
Extraction
Often the most difficult for mobile forensic investigators is the collection of the device. In the case of KaiOS devices it is a mix; the extraction logically is uncharted territory by tool vendors and it has been found to be much easier to simply obtain a physical collection. Why is this you ask? Let me cover briefly some of the anomalies with devices running this emerging operating system.
- ADB is available after USB debugging is enabled, and basic information can be obtained with the typical ADB command interface.
- However, since this is not an “Android” device tools are unaware of how to query to obtain the most basic of data (e.g., calls, SMS/MMS, contacts) by using an agent.
- Binary collection is unencrypted and by enabling download mode on the device running KaiOS a full physical is obtainable.
- Web based data has storage principles and locations not like a device running Android and tool manufacturers are having to R/D from square-one.
So, if you can easily obtain a physical collection then what is the big deal right? Well, it comes down to parsing and decoding of the data; most forensic tools in the market are having a difficult time. The information on parsing and decoding will be covered in part 2 of this document. However, let me cover a general method of obtaining at least the binary image from a KaiOS device.
Debugging
The first addition of the KaiOS devices that hit the market in 2017 and some of the Reliance Jio devices can be put into debugging mode by using the same method as other Android devices. Navigate to the device information and click on the build version to then show developer options. It has been my experience that the devices sold in North America as “Burners” do not have this option and an engineering passcode has to be used. The code *#*#33284#*#* (spells DEBUG) entered by dialing will place the device into debugging mode and once connecting the cable the device will be visible in the Device Manager. This has been tested on the most popular smart feature phone Alcatels (MyFlip (405), Go Flip/QuickFlip(4044), SmartFlip (4052). With all these devices ADB was enabled and I was able to query and communicate to the device via the command window with ADB. (More on this in Part 2)
Extraction
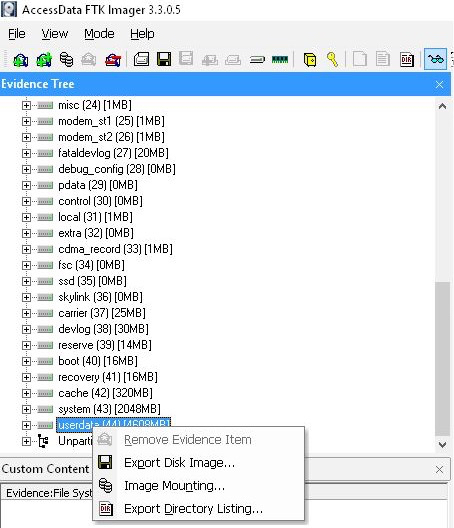
Obtaining a physical is as simple as placing the device in download mode and running your software of choice so long as it supports physical collection of devices with Qualcomm Snapdragon chipsets 210 (MSM8909). Some software simply allows using a cable, commonly referred to as an EDL cable, but I have found many of these Alcatels have to be forced into download mode then connected. Make sure before beginning the process to download and install the Qualcomm QDLoader driver if your software of choice has not preinstalled these required drivers. Here is a location of a guide on how to install a setup package and also what should be expected in the Device Manager when the attached device is recognized.
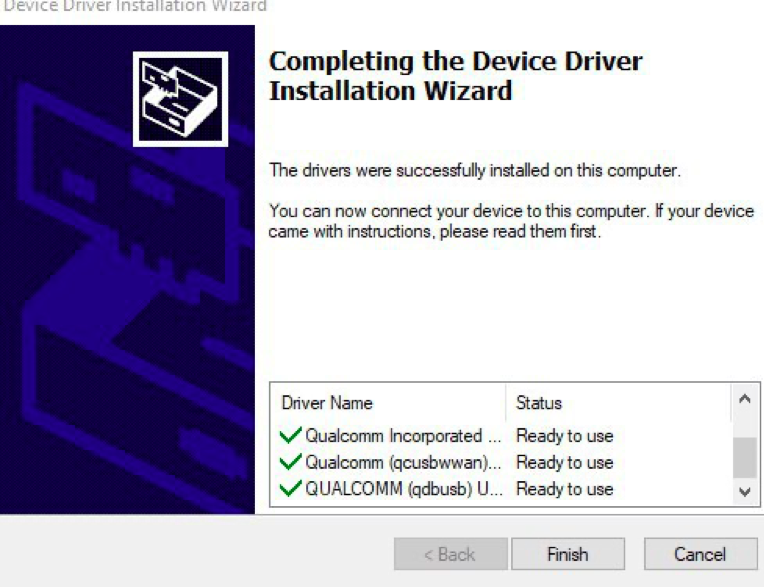
Remember the device will not be recognized until plugged into the examination computer. So, by using a combination of key presses with the Alcatel device and then plugging the device into the computer running your collection software we can obtain a full physical. With the Alcatel devices follow the following steps:
- Remove the battery and then re-insert the battery but leave the device off.
- Press both the + and – volume keys (simply press between them both).
- Plug the cable into the device and then while plugging into the USB on keep the volume keys depressed.
- The device will start up and goto the download mode screen on the main LCD.
- Press the volume up + and the screen will go black.
- Continue to hold for approximately 10 seconds while drivers will begin to load
- The device will then be located under the ports section in the Device Manager
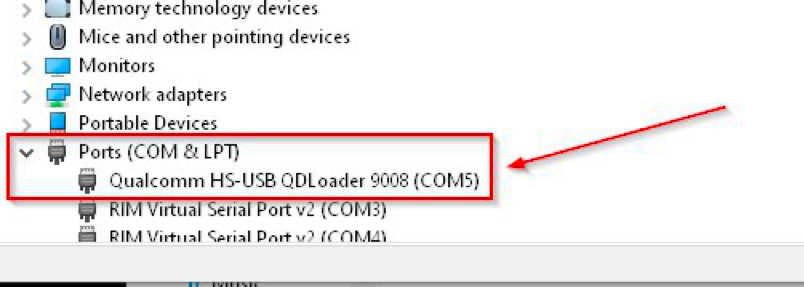
Once the device is recognized in the Device Manager, the device can be collected at a physical level. In this instance I used the Jio Profile in Oxygen Forensic Detective to extract the partitions into a binary file. The binary file was then processed and decoded in the same solution.
In PART 2 (and the most important) I will walk through the parsing and decoding of the data and where to look for some great artifacts.
Thank you, look for Part 2 soon! Until next time, and never stop learning!

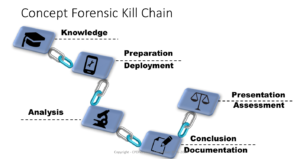 I introduced my kill chain concept to a great group at TechnoSecurity this week. It is a concept that I mashed from the military definition as well as that of the 2011 cyber kill chain of Lockheed Martin.
I introduced my kill chain concept to a great group at TechnoSecurity this week. It is a concept that I mashed from the military definition as well as that of the 2011 cyber kill chain of Lockheed Martin.
 In the previous post we discussed the need to be vigilant in the analysis of app data obtaining from today’s mobile devices. Furthermore, I made it clear that mobile forensic software is not the end all solution to your app overload as a forensic examiner. The probability that an examiner will be faced with the dissection of an unsupported app is quite great. This post will take it a step further and help to point out, at least in a most basic way, how an examiner can uncover valuable data without relying on the automated solution “at all costs”.
In the previous post we discussed the need to be vigilant in the analysis of app data obtaining from today’s mobile devices. Furthermore, I made it clear that mobile forensic software is not the end all solution to your app overload as a forensic examiner. The probability that an examiner will be faced with the dissection of an unsupported app is quite great. This post will take it a step further and help to point out, at least in a most basic way, how an examiner can uncover valuable data without relying on the automated solution “at all costs”.
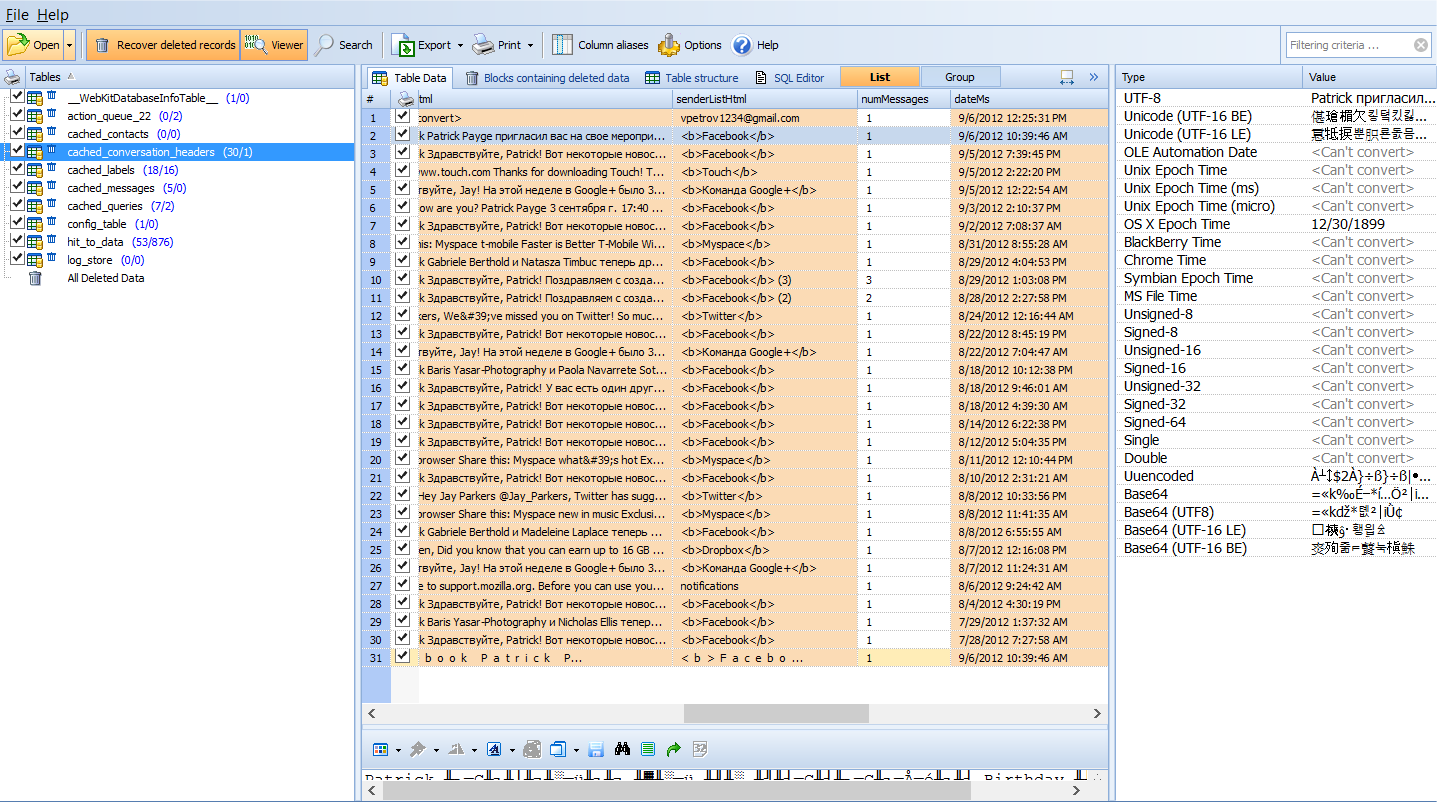
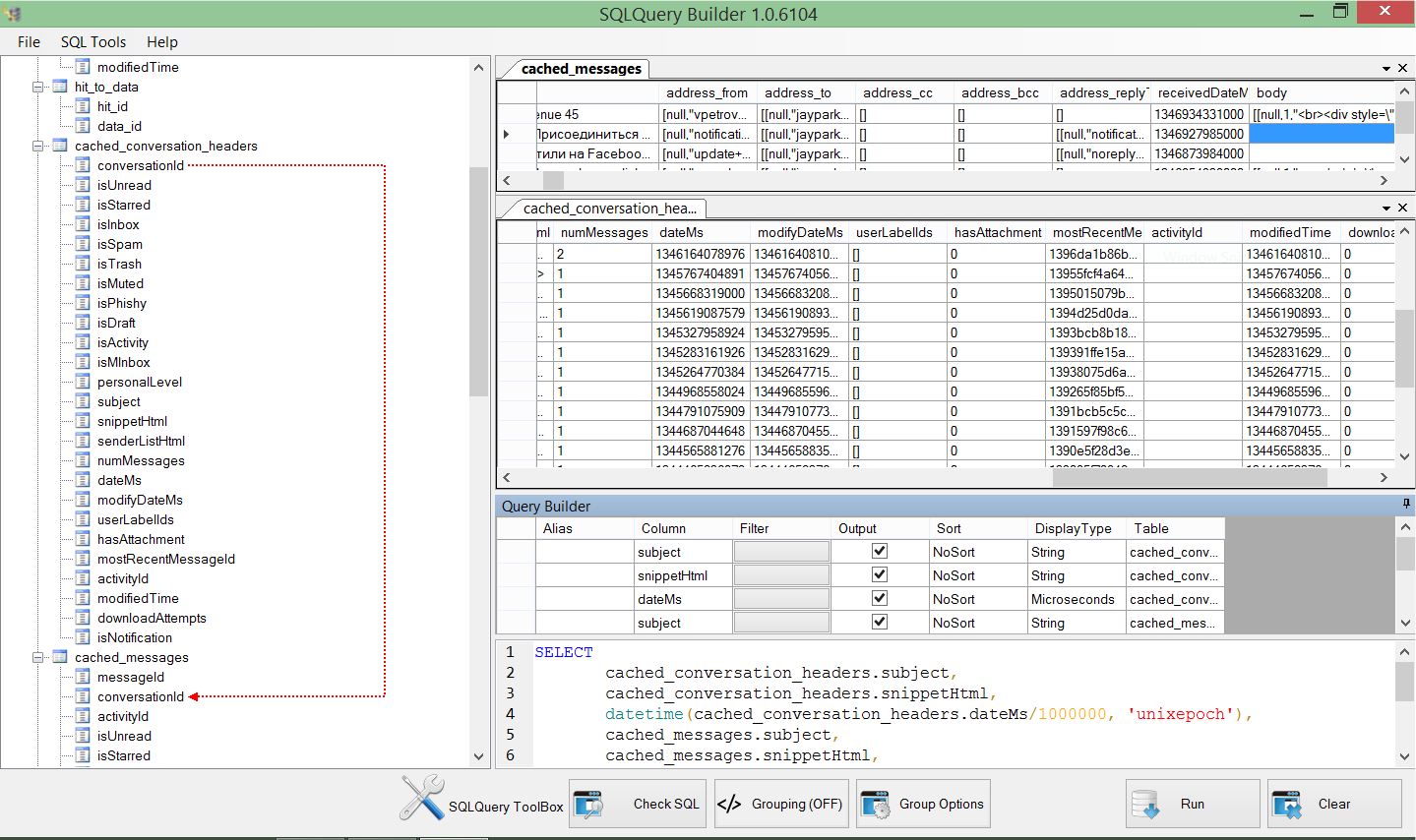
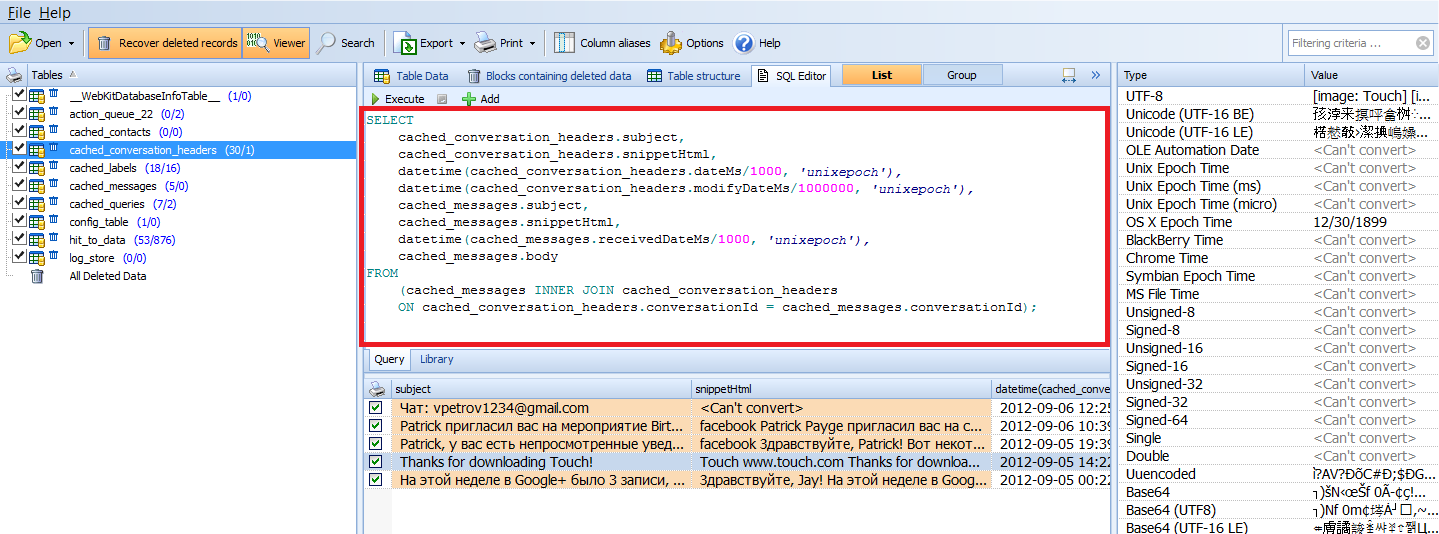
 Today’s mobile forensic solution landscape is a battle of supported apps, and a race to give to the examiner a version that will decode a parse a particular app that is paramount to that case, on that day. However, statistically speaking having an almost psychic ability to determine today’s paramount app is about the same as guessing the winning lottery numbers for each lotto across the US everyday! Simply speaking, today’s popular app might not be tomorrow’s, and when it comes to examining data in a case it is always an unsupported third party app that is involved. More frequently than not, the examiners are examining apps that are not the most popular and most of the time it is the first time they have even heard of the app, let alone examine.
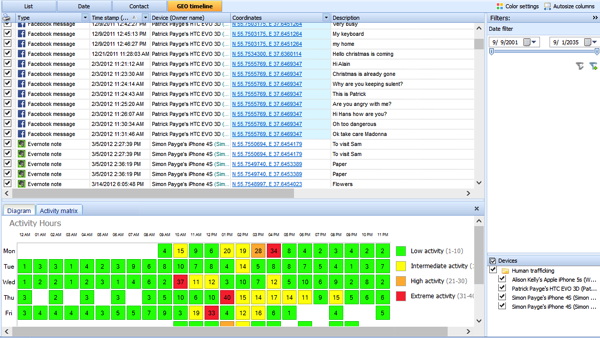
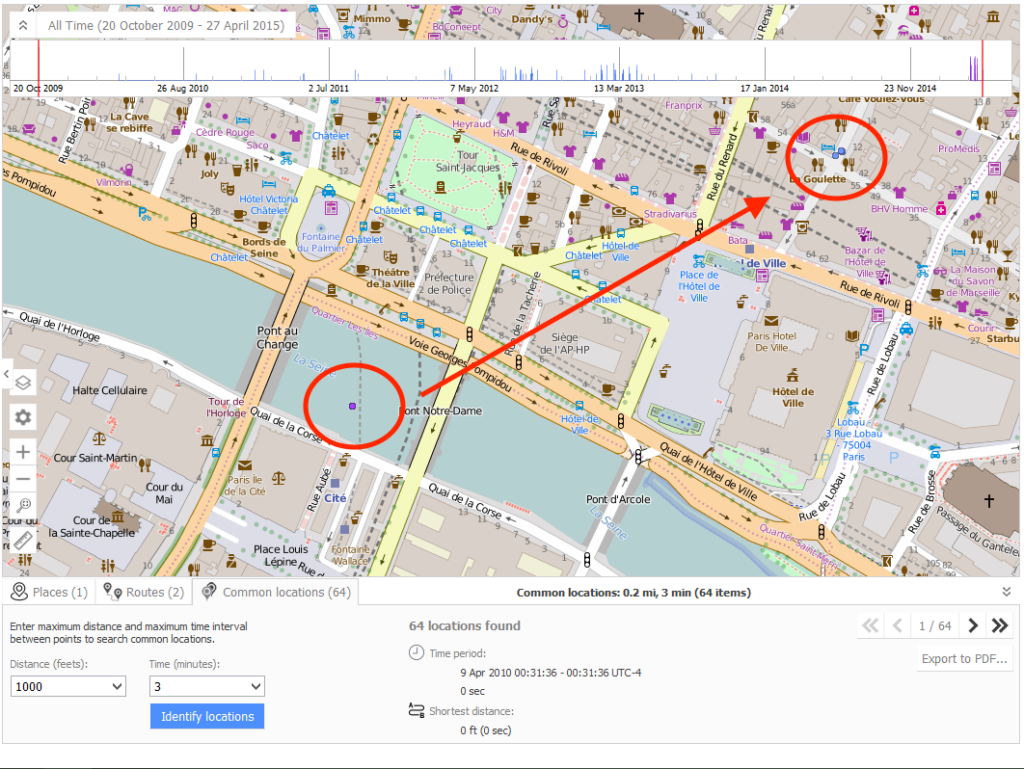
Today’s mobile forensic solution landscape is a battle of supported apps, and a race to give to the examiner a version that will decode a parse a particular app that is paramount to that case, on that day. However, statistically speaking having an almost psychic ability to determine today’s paramount app is about the same as guessing the winning lottery numbers for each lotto across the US everyday! Simply speaking, today’s popular app might not be tomorrow’s, and when it comes to examining data in a case it is always an unsupported third party app that is involved. More frequently than not, the examiners are examining apps that are not the most popular and most of the time it is the first time they have even heard of the app, let alone examine. It is all in the name —mobile device. These two words tell you, the reader, that it is a device that is mobile. By mobile it simply implies that the device can be anywhere. In an effort for the device to be “aware” of the location for cellular and data reception it must seek out where in the world it might be. This is just how the mobile device works, and must work. If you believe that this is not the truth just turn off Wi-Fi, Bluetooth, and cellular (turn on airplane mode). Go outside and open up Google maps or Apple Maps and walk around. You will quickly see that your blue dot is still being tracked. However, if you turn off Location Services AND place in Airplane mode then you will be prompted to allow to get a current fix and denying this feature will in fact put you “somewhat” off the grid. However, no one wants to turn their mobile device into a simple music player, so valuable location data is always available when conducting mobile forensic examinations.
It is all in the name —mobile device. These two words tell you, the reader, that it is a device that is mobile. By mobile it simply implies that the device can be anywhere. In an effort for the device to be “aware” of the location for cellular and data reception it must seek out where in the world it might be. This is just how the mobile device works, and must work. If you believe that this is not the truth just turn off Wi-Fi, Bluetooth, and cellular (turn on airplane mode). Go outside and open up Google maps or Apple Maps and walk around. You will quickly see that your blue dot is still being tracked. However, if you turn off Location Services AND place in Airplane mode then you will be prompted to allow to get a current fix and denying this feature will in fact put you “somewhat” off the grid. However, no one wants to turn their mobile device into a simple music player, so valuable location data is always available when conducting mobile forensic examinations.