For some time now the talk in the mobile forensic world is all about ISP, JTAG, and chip-off. Let us take a look at what people are really talking about, why having an understaning of these methods is critical, and most importantly how to get to the artifacts when your mobile forensic tool balks when trying to import.
From Mobile Forensic Investigations: A Guide to Evidence Collection, Analysis, and Presentation the word “JTAG” (Joint Test Action Group) has a variety of meanings, from directly programming systems to debugging others, from Xbox hacking to forensics. In the context of the book, JTAG is described as the process of setting and reading values on the test pins accessible on the PCB of the mobile device. By using the TAPs, communication can occur via the boundary-scan path, interfacing with the Boundary Scan Registers (BSR) that interface with components on the PCB. These components can be programmed or read without the removal, independently reading, or programming each separately. (pg. 136) ISP (In System Programming), like the “JTAG” method use the TAPs, allowing communication direclty bypassing the CPU to collect the RAW binary image of the mobile device.
The removal of a device’s flash memory module and analyzing it is referred to as “chip-off”. The chip-off procedure is quite labor intensive in both the removal of the actual embedded flash memory chip and also reading of the stored data. Because of the various differences between phone models and storage types, that could range from Thin Small Outline Package (TSOP) to Fine-pitch Ball Grid Array (FBGA), the purchase of the equipment to read the information from the embedded chips and the time investment can become expensive. However, conducting the imaging of the memory chip using this method is the closest to the bit-by-bit collection a forensic examiner would expect and is similar to imaging a computer’s hard drive. (pg. 140)
It is imperitive that experts understand the methods to accomplish these types of collections as it is often the only way to have success. Simply because with today’s mobile device security provisions it is often the only way to access the coveted user data. For this technical and specialized skill it is extremely important to receive training prior to attempting these type of extractions. Okay, so you have received the training or a binary image from one of the afor mentioned techniques; now what?
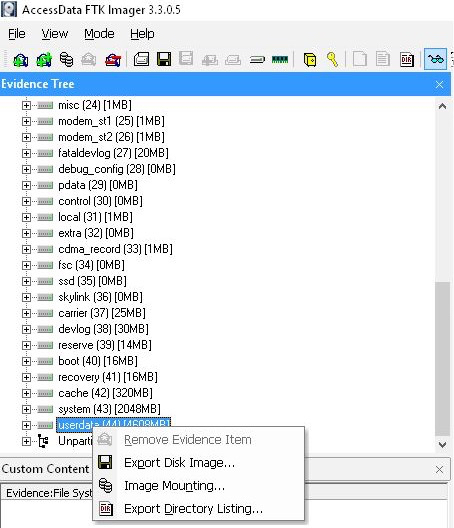
Since the image is a binary file it will need to be recongized in the mobile forensic tool of choice. Often, experts have the file but find when they import the file into their tool of choice problems begin. They are simply given an error indicating that the file could not be recognized. Take an Android device for example. Since Android devices contain a varied number of “partitions” the mobile forensic tool often cannot decern the offset of the important userdata partition from the partition table. When this occurs using the following solution can help to at least obtain data from this valuable area.
Using the free tool FTK Imager from AccessData, import the binary file as an image. Immediately the file will be expanded and decoded to show the varied partitions. Locate the userdata partition, select it and right click. Select from the context menu Export As Image. Give the image a unique name, save the format as raw, and add 0 to Image Fragment Size (Figure 1-1). The 0 in Image Fragment Sizeis important as breaking up the image into several files will not allow for the sucessful import of the image by most mobile forensic tools. Once the image is created it can be imported in as a Android Physical/JTAG image by tools such as Oxygen Forensic Detective to allow for complete parsing an decoding of valuable user data.
This technique is just one way to get to the valuable data within a binary image created by JTAG, ISP, and Chip-off techniques.
Thanks for reading and please subscribe.