It is all in the name —mobile device. These two words tell you, the reader, that it is a device that is mobile. By mobile it simply implies that the device can be anywhere. In an effort for the device to be “aware” of the location for cellular and data reception it must seek out where in the world it might be. This is just how the mobile device works, and must work. If you believe that this is not the truth just turn off Wi-Fi, Bluetooth, and cellular (turn on airplane mode). Go outside and open up Google maps or Apple Maps and walk around. You will quickly see that your blue dot is still being tracked. However, if you turn off Location Services AND place in Airplane mode then you will be prompted to allow to get a current fix and denying this feature will in fact put you “somewhat” off the grid. However, no one wants to turn their mobile device into a simple music player, so valuable location data is always available when conducting mobile forensic examinations.
It is all in the name —mobile device. These two words tell you, the reader, that it is a device that is mobile. By mobile it simply implies that the device can be anywhere. In an effort for the device to be “aware” of the location for cellular and data reception it must seek out where in the world it might be. This is just how the mobile device works, and must work. If you believe that this is not the truth just turn off Wi-Fi, Bluetooth, and cellular (turn on airplane mode). Go outside and open up Google maps or Apple Maps and walk around. You will quickly see that your blue dot is still being tracked. However, if you turn off Location Services AND place in Airplane mode then you will be prompted to allow to get a current fix and denying this feature will in fact put you “somewhat” off the grid. However, no one wants to turn their mobile device into a simple music player, so valuable location data is always available when conducting mobile forensic examinations.
Location data can give us information to include but not limited to:
- Photo coordinates
- App usage
- Cellular usage
- Wi-Fi usage
- Driving directions
Photo coordinates
Location information is stored in the EXIF (Exchangeable Image Format) data of a photo. This data may contain the device information, weather conditions, latitude/longitude, focus, and other markers. As indicated the latitude and longitude of images can be within the EXIF which can help to identify the location the image was taken with the mobile device. With the ability to sharing SD cards with Android devices the investigator should be cognizant of the additional information (i.e., device information) before indicating what device took the picture. Also, EXIF data does not have to be included in the image. If the photo was sent or received the EXIF data is often the first information to be removed in the compression process. This is simply done by many social networks to allow for better speed and network performance. Massive images would be a serious bottleneck in the system. However, a user can also elect to not include location information using a global setting in both iOS and Android devices. This could also be the case as to why an investigator might not see location information within the EXIF metadata.
App usage
Apps within a mobile device are a treasure trove of significant case data. With over 80% of today’s users using at least one social app to communicate there is no reason an investigator should not be going through all apps on a mobile device. Also, many have location services built-in when the app contains a picture/video capability, directions, business lookup, business check-in, or other location type services. Also, in an effort to allow the device to work better in areas of low network bandwidth things like Bluetooth and Wi-Fi are employed so the device must report general location as well. Take a look at: /data/com.google.android.apps.maps/databases/search_history.db. This database records the searched locations within the Google Map app, storing the latitude and longitude along with a timestamp. This data is in the suggestions table in the SQLite database.
Cellular usage / Wi-Fi usage
Android devices cache a tremendous amount of general location data to “help” their users have a better experience. An example from Mobile Forensic Investigations is the /preferences/SystemConfiguration/com.apple.network.identification.plist. This property list contains the IP addresses used and assigned to the iOS device when
communicating on both the cellular WAN and Wi-Fi. This property list can be fantastic for any investigation. iOS devices also cache location information in the form of cellular and Wi-Fi usage to assist it’s many users with better performance. However, many automated tools do not parse or analyze this file along with many other location and settings files. An investigator armed with the ability to manually harvest these types of artifacts can often make considerable contributions to the overall investigation.
Driving directions
A given for any investigation—remember we no longer use map books bought at the nearest convenience store. Everyone uses some type of direction app, even if they do not drive. I do not know how many times I have used Google Maps to look up an address in another country that I was walking to, or looking to see how far it was. What great evidence if an investigator is looking for commonalities with a crime and a location. Did the person research the location prior, obtain driving directions, or any other nugget?
Location information is extremely powerful in any investigation, but can be the smoking gun in cases involving two or more devices. Imagine this: While conducting an interview of two people, both say they do not know one another and have never seen each other prior to today. The investigator has seized both mobile devices and began the tedious process of working through the information. By reviewing the location data, using a timeline of events, the investigator can quickly see that the two individual devices, who are not from France, but believed to be involved in terrorist activities were .3 miles from each other within 30 minutes of each other (Figure 1 and 2). The “heat map” shows to the examiner the day and time the devices are most active. Further investigation revealed that both devices were in London’s Heathrow airport two days prior, just 10 minutes apart and in the same terminal, and the following day at a small cafe at the same time. Even though the subjects did not speak to one another this location information clearly shows the devices they had possession of were in close proximity of each other on three independent days prior to the attack.
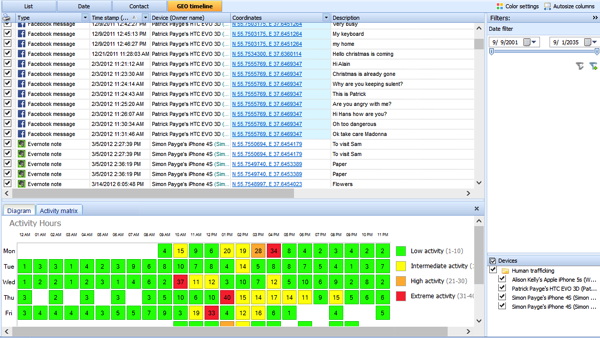
Figure 1: Timeline using geo-data from multiple devices
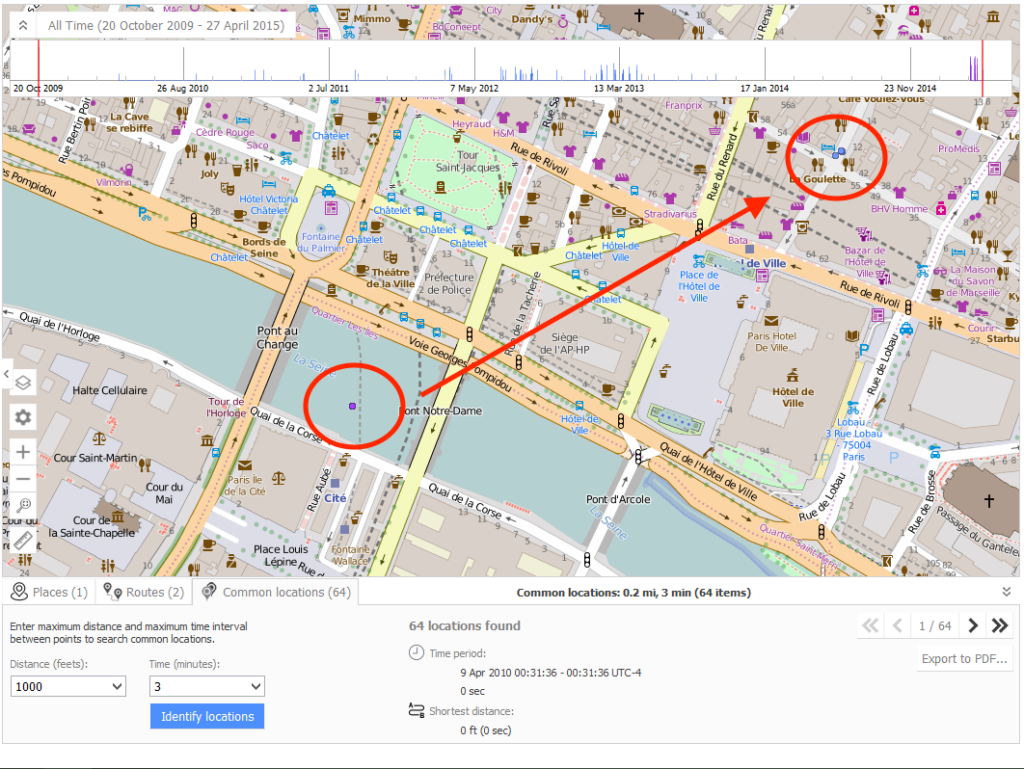
Figure 2: Mapping two or more devices to show common locations.
Having the ability to quickly build a timeline and immediately display extracted location information is critical. With this data, an investigator can quickly build credible information that can often shed new light to any investigation. The collection of the device is typically what many investigators believe is the most difficult. I would disagree. I believe the analysis of data is often the most overlooked simply because many believe the automation will recover all that can be recovered. The analysis of critical files is more often a manual process, and no file should not be overturned. Many of these most critical files are described in Mobile Forensic Investigations: A Guide to Evidence Collection, Analysis, and Presentation available on Amazon and many other outlets. Today’s mobile devices will be used in every type of crime and subsequent investigations must step up to the data that can be extracted and analyzed.