In the previous post we discussed the need to be vigilant in the analysis of app data obtaining from today’s mobile devices. Furthermore, I made it clear that mobile forensic software is not the end all solution to your app overload as a forensic examiner. The probability that an examiner will be faced with the dissection of an unsupported app is quite great. This post will take it a step further and help to point out, at least in a most basic way, how an examiner can uncover valuable data without relying on the automated solution “at all costs”.
In the previous post we discussed the need to be vigilant in the analysis of app data obtaining from today’s mobile devices. Furthermore, I made it clear that mobile forensic software is not the end all solution to your app overload as a forensic examiner. The probability that an examiner will be faced with the dissection of an unsupported app is quite great. This post will take it a step further and help to point out, at least in a most basic way, how an examiner can uncover valuable data without relying on the automated solution “at all costs”.
In this bloggercise we will examine a SQLite database from built in browsers of both Android and iOS file systems. As I mentioned in the previous post, the examiner has to go the extra mile if they are to find the 0’s and 1’s in the digital haystack. These examples can be used with any SQLite database that an examiner might run into during the investigation.
Let me first state, running a set of search queries to identify relevant material for the case is a necessity. I find it extremely beneficial to use Oxygen Forensic® Detective to search a list of words not only over the database, but also within the files. Searching within files is a necessity to uncover strings within database files that are not fully supported, not supported at all, or simply not decoded. This way the examination has a clear scope and wandering around the file system is keep to a minimum with hyper-focus.
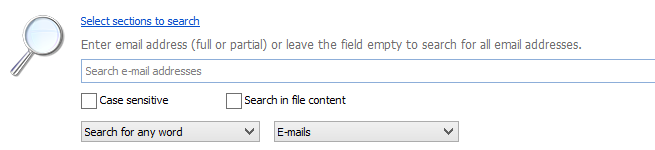
Figure 1: Search for email addresses
Figure 2: Database within an app that is fully user action created.
Once you have your hits and are focused on the files of interest the examination of these files can start. In my example in Figure 1 I used a regular expression ((\W|^)[\w.+\-]{0,25}@(yahoo|hotmail|gmail)\.com(\W|$)) to search for free (i.e. gmail, yahoo, hotmail) email addresses in an effort to uncover any additional addresses of interest. With this search I uncovered an email address within a database file within the Android built in browser. What is interesting is the fact this database is not the stock database for the android browser, but rather a database created by the application for storage of mobile enabled websites. “What? You say a website within a browser that stores data?” Much like a Russian hallow doll that continues to contain a replica of the doll that housed the smaller doll, and so on. Browsers are ripe with databases similar to this example when the WebKit platform is utilized. The fact that these types of databases are not processed by mobile forensic solutions is an important fact to remember. So, if a user used the browser to surf their Facebook account, the examiner will surely miss this data if they are simply looking at the Facebook app that was parsed by the mobile solution. This is a nuance artifact housed in this particular Android browser that very few even realize or even understand. Again, the critical take-a-way is to comprehend the idea that modern mobile browsers from iOS to Android are packed with these user created manifestations, but few solutions have the ability to even recognize this valuable artifact, let-alone automatically parse the information.
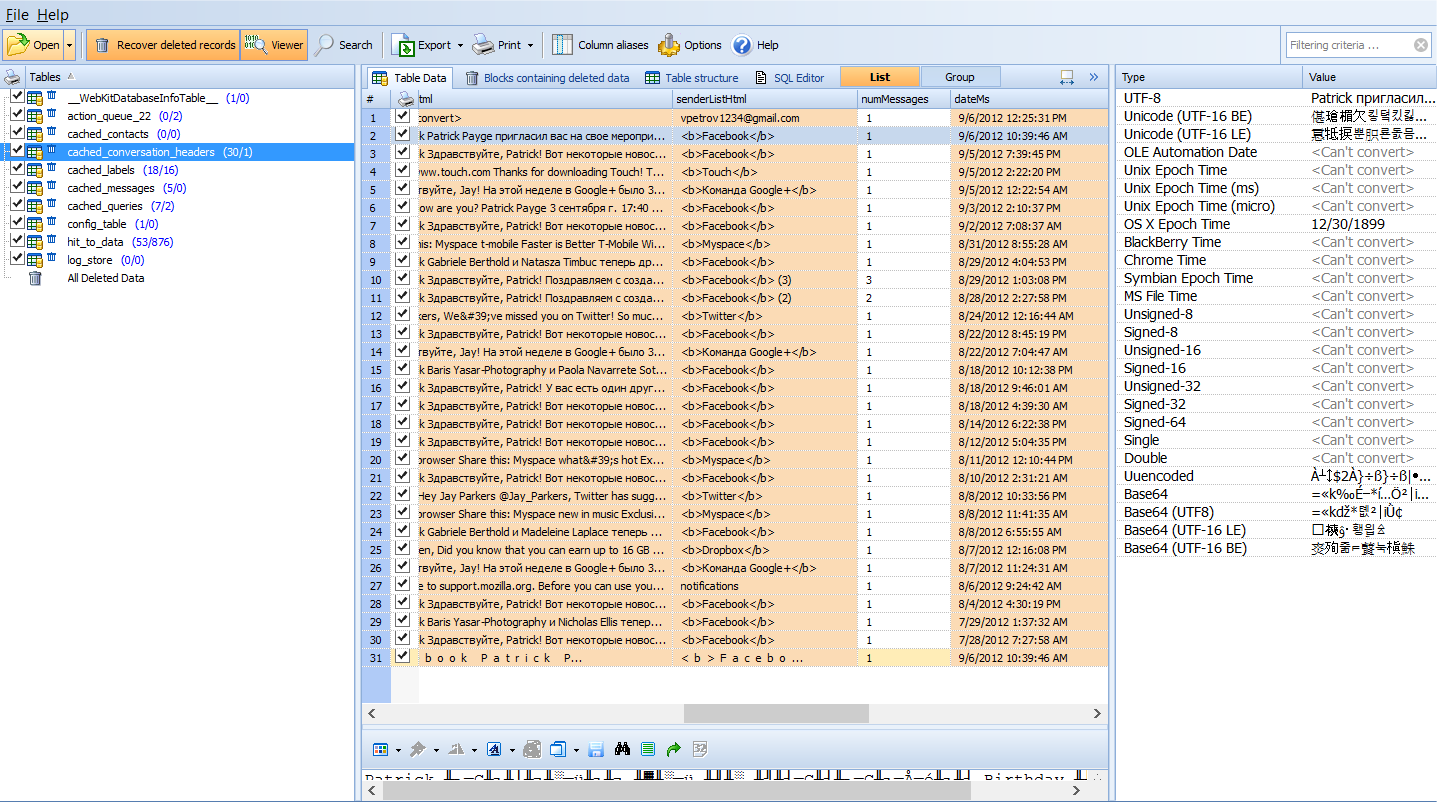
Take for example the file in Figure 3 viewed in Oxygen Forensics® SQLViewer. This file hosts content (yes content) of gmail messages. Not just the snippet HTML but the actual message in it’s entirety. Granted, the data in the database is only going to be the most recently cached emails when the user visited their email account, but it is possible it contains information critical to your case and no modern tool at this date will parse and decode this information automatically. This is not the gmail app, but the user accessed their gmail page from a browser. Now, since there are multiple tables that make up a database file, and Oxygen Forensic® SQLite Viewer can execute SQL Queries, but will not build without knowledge of SQL I use another tool in conjunction. Yes, this means the expert must take additional steps to decode this information.
Figure 3 : Single table of Webkit database found in Dolphin Browser for Android.
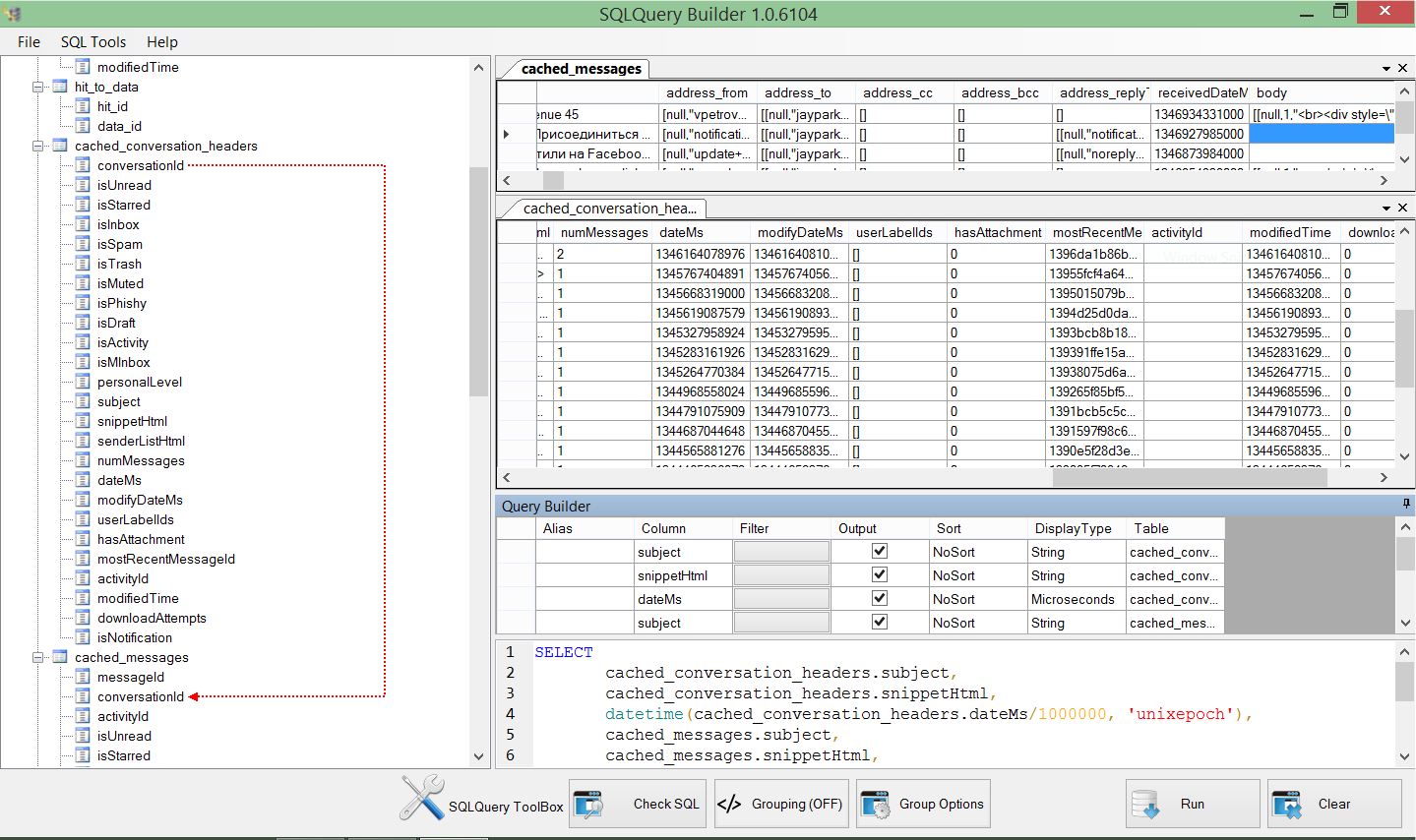
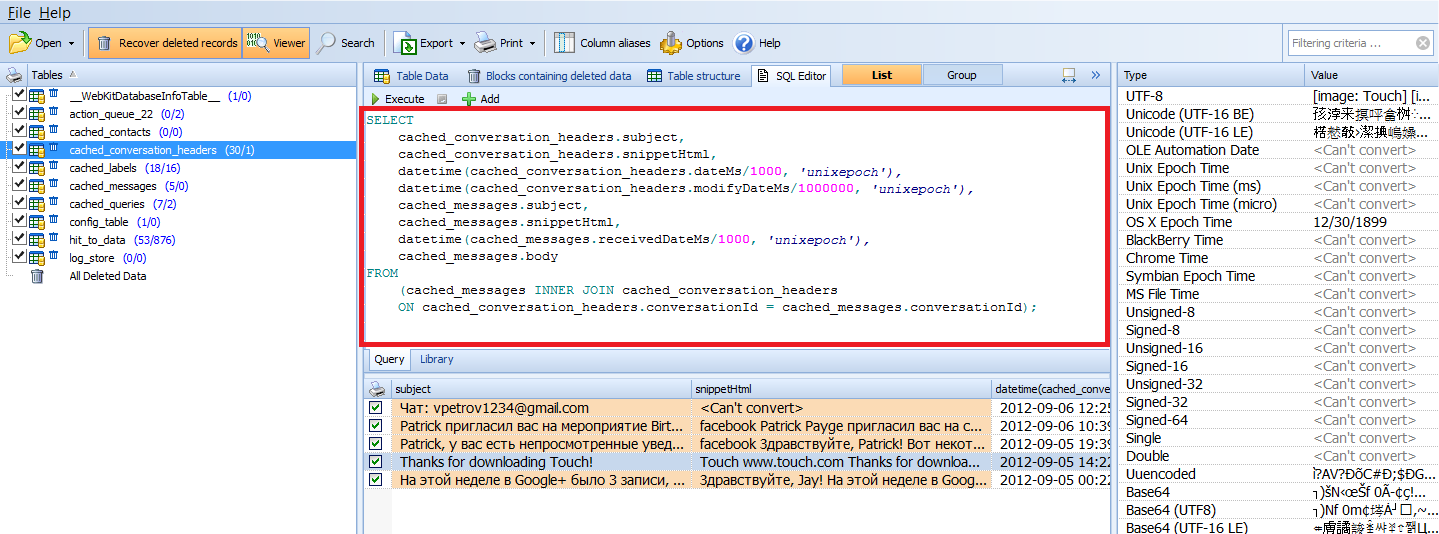
Using the CPDForensic SQLQuery Builder I am able create complex SQL queries and JOINs, convert date/time, and more. By JOINing TABLES within the database, the expert can make sense of the data quickly as observed in Figure 4. Now, the expert can copy and paste the created SQL command into Oxygen Forensic® SQLite Viewer (Figure 5) and see the fantastic results; a created command to support an app database that has not been supported before! The query can also be executed in the SQLQuery Builder to produce a report if Oxygen Forensic® Detective is not a tool in the forensic toolbox. In both the SQLQuery Builder and Oxygen Forensic® SQLite Viewer the expert can even save the query to use against another gmail database that they might run into during a later examination.
Figure 4: Complex SQL Query created using CPDForensics SQLQuery Builder.
Figure 5: Complex SQL Query from SQLQuery Builder now used in Oxygen Forensic® SQLite Viewer, creates a powerful query over multiple tables.
Data within the browser application folder is so subjective it becomes difficult for a mobile forensic tool to conform to uncovering these artifacts. Also, these treasure troves are created on the fly, per the user’s activity. Now, throw in the multitude of internet browsers available for a mobile device it becomes an impossibility that the mobile forensic solution of choice will be able to parse and decode this data in all situations. Again, it comes down to the expert behind the keyboard and their commitment to performing a complete examination.
The likelihood an examiner will run an unsupported app, or even the supported app that is not entirely decoded and parsed is quite great. However, the likelihood that data will remain hidden, unanalyzed, and undocumented by the expert should be slim so long as the will to seek and decode is great.