 I introduced my kill chain concept to a great group at TechnoSecurity this week. It is a concept that I mashed from the military definition as well as that of the 2011 cyber kill chain of Lockheed Martin.
I introduced my kill chain concept to a great group at TechnoSecurity this week. It is a concept that I mashed from the military definition as well as that of the 2011 cyber kill chain of Lockheed Martin.
The developing concept comes down to a failing belief that one can just “wing it” when conducting digital forensics, particularly, mobile device forensics. Understanding my concept is both offensive and defensive in nature, an examiner (both as a defense expert and state expert) can quickly see what areas can quickly cause an investigation to spiral out of control.
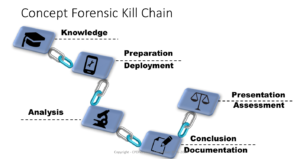
We walked through the process of knowledge -> preparation/deployment ->analysis -> conclusion/documentation -> presentation/assessment as displayed in the graphic. By understanding a break at any point in the chain can ultimately jeopardize the case/examination the attendees quickly realized current procedures need to be updated and/or actually created. Ending the lecture on an actual case study in which a break in the forensic chain resulted in an acquittal-again offensive and defensive measures.
I outlined to the attendees that this concept is theory and to be used as a guideline to better the processes and procedures that currently plague mobile forensic examinations. Many procedural modifications can be inserted into this model to overcome additional pit falls, but the fact remains – we need to be and do better.
My subtitle says it all : The strongest missions rely on the strength of the weakest link
Identify your weakest link in the forensic kill chain and work hard to make it stronger each examination.
