When I started my pilgrimage into mobile forensics, I did so with the goal of providing the law enforcement community with the tools and training that would assist investigators in extracting relevant data from cell phones. Back then, mobile forensics was limited to obtaining contact lists, SMS messages, and sometimes call logs. This information helped solve many cases. It also solidified the fact that data living on mobile devices was a potential source of evidence waiting to be discovered.
As my own mobile forensics training progressed, so did the technology of mobile devices. In a relatively short period of time, cell phones and mobile devices were no longer used only to send text messages and make phone calls. Mobile devices were now used to send and receive emails; send and receive MMS message with file attachments; take photos and videos using the device’s camera; store images, videos, and other media; browse the Internet; and communicate with others using an ever increasing number of software applications or apps. With these enhanced capabilities came the possibility of obtaining additional evidence such as EXIF data from images stored on a device, internet browser history, Wi-Fi locations used to access the Internet, stored passwords, and more.
A bottleneck in the forensic community was inevitable as we struggled with too many devices, too many data types, and too few options in the collection of mobile device data. The technology of mobile devices was progressing more rapidly than advancements in the development of mobile forensics tools. As a result, I was forced to rely on manually parsing the data. I focused my training on extracting, manually locating and converting the data into a readable format, and making it presentable in court. This is where scripting for me started. I wanted to automate the repetitive task of manually parsing data.
Fast forward to today. Mobile forensic tools are still inept in properly parsing and displaying all the data that might be available on a mobile device. This is not the fault of the mobile forensic tool, but the fault of a rapidly changing mobile device environment. Since software is written by a developer in real time, developers are already behind before they even start coding a single line. This is a fact that no software company would deny. I have always believed that “in order to be prepared for tomorrow you have to think about tomorrow today.” Today is no different. This is the reason why MPE+ has evolved to allow the examiner to adapt to today’s problems in real time. MPE+ provides tools that can be customized to adapt to changes and address challenges faced by the examiner at any time. Investigators do not have to wait for a software upgrade, but can utilize MPE+’s tools already at their disposal.
With this in mind, MPE+ includes the pythonScripter. PythonScripter was developed to give the examiner a way to support data extraction, parsing and reporting of mobile device data without waiting for the software developer to create the code. The MPE+ pythonScripter allows the examiner to create, import or use preconfigured python scripts against any data imported into the MPE+ interface. This allows MPE+ to support an unlimited amount of devices, unlimited data types for carving, unlimited extraction support of image location data, unlimited extraction support of meta data and more. With pythonScripter, MPE+ can even support the parsing, conversion and reporting of data from a phone born today.
As an example, we can say MPE+ does not directly support GPS devices. However, utilizing a physical image of a GPS device obtained with MPE+, we can use the file system view to navigate the folder containing the GPX data. Once the folder of interest is located, we can right click on the folder selected from the predefined selections and parse the GPX data. (Figure 1)
- pythonScripter Selection
Figure 1
Using the pythonScripter dialog we can select a predefined python script, or build one to parse and display the critical data from the GPX file. (Figure 2)
Figure 2
Both waypoints (Figure 3) and track points (Figure 2) can be parsed. Therefore, artifacts like time, elevation, latitude, longitude and even waypoint name can be extracted.
- Latitude and Longitude Output
Figure 3
The data can now be overlaid onto a map to visualize the waypoints, route or track. (Figure 4)
Figure 4
As we know, the location information can benefit any examination. The location information is used not only in GPS devices, but applications on mobile devices and images taken by those devices as well. When using a python script that extracts location information from images, a user can identify the location where the picture was taken and quickly plot this location on the map. Also beneficial is the fact that investigators can develop a script to look into every file on the mobile device; including file headers, file types, and even data and code strings. Once these scripts are created they can be further customized or edited by the user at any time.
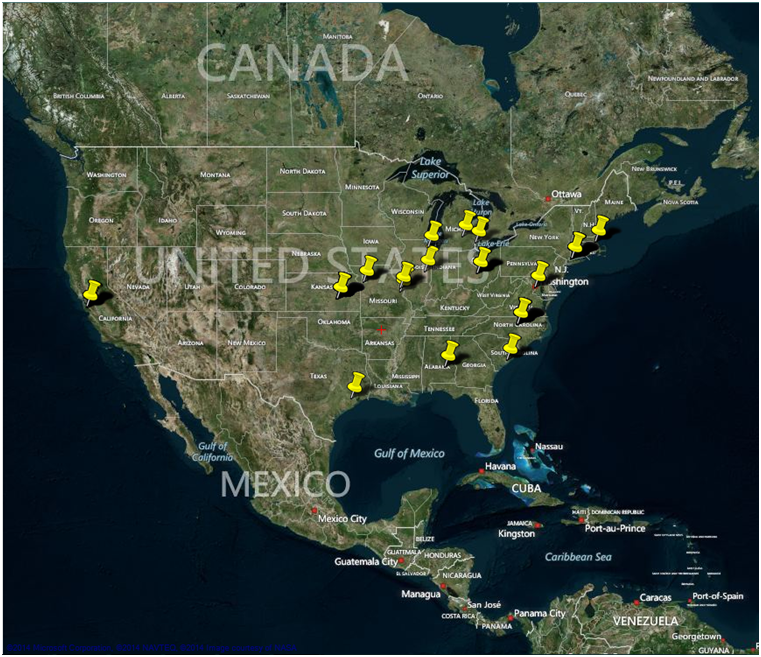
A perfect example of customized scripting would be, utilizing a previously written script to locate all the IP (Internet Protocol) addresses on a Facebook account by the use of regular expressions. To do this, users can simply right click on the com.facebook.katana folder and select pythonScripter. Utilizing the browse button, users can choose the previously written script to iterate through all the files and folders and identify a particular pattern. The customized script we utilized for this example quickly located the IP pattern and displayed the file names containing various IP addresses found in the Facebook application files (Figure 5). Users can then map these IP addresses to a map module for visualization. (Figure 6).
- IP Addresses parsed
Figure 5
- IP Pin Map
Figure 6
With the pythonScripter, the power of uncovering maximum data is at your fingertips. Prior to the development of MPE+’s pythonScripter, these advanced automated analysis capabilities were not possible.
Data carve any file, extract critical data no other tool can extract, and put a mobile device at the scene by extracting location information quickly and automatically are just a few features that can be accomplished only with MPE+ and the pythonScripter.
The pythonScripter is just another example of how MPE+ is introducing an entirely new approach to mobile device forensics.






Pingback: Cell Phone Training | Cell Phone Training And Reviews
Pingback: Gregory Smith