 I helped with a couple of posts in the last month that dealt with International Mobile (Station) Equipment Identity (IMEIs) produced and displayed by both mobile forensic software and also by the carriers themselves. The assistance was primarily dealing with examiners finding a discrepancy with what the carrier was showing in Call Detail Records (CDRs) and what was produced by the mobile forensic software and even the identification label on the device themselves. Lets cover a little bit of information on IMEI numbers first.
I helped with a couple of posts in the last month that dealt with International Mobile (Station) Equipment Identity (IMEIs) produced and displayed by both mobile forensic software and also by the carriers themselves. The assistance was primarily dealing with examiners finding a discrepancy with what the carrier was showing in Call Detail Records (CDRs) and what was produced by the mobile forensic software and even the identification label on the device themselves. Lets cover a little bit of information on IMEI numbers first.
IMEI numbers are used as a serial number for the device. Much like the serial number you might find on other items like cameras, TVs and stereos. However, the IMEI is also used by the mobile carrier to identify the device over the cellular network via the Equipment Identity Register (EIR). This helps to deliver content, assist with subscriber to equipment correlation, equipment maintenance and equipment allocation.
The IMEI is a 15 digit number composed of several subsections: Type Allocation Code (TAC), Serial Number(SN) and a Check-Digit(CD). Since 2004 however IMEI Software Version numbers or IMEISV are being used to assist with a carrier’s identification of the software version running on the device. This feature can assist with upgrades, notification to users and maintenance of the user device by the carrier. This number is composed of the TAC, SN and SV for a total of 16 digits (sometimes 17). The check digit is generally dropped from the IMEISV. The check digit can be calculated, if missing, by dropping the SV digits and using Luhns Algorithm against the remaining digits starting at the right most digit. The layout of both the IMEI and IMEISV is described below.
T = TAC digit
N = Serial Number digit
C = Check Digit
S = Software Version digit
IMEI = TTTTTTTT-NNNNNN-C
IMEISV = TTTTTTTT=NNNNNN-SS
What becomes confusing to examiners is the fact that some mobile forensic software will report two IMEI numbers and identify one as the calculated and the other as the IMEI. Furthermore, telco carriers will often send back CDRs that display the IMEISV and not IMEI. Since they are slightly different (last two digits typically) the comparison with the IMEI that is listed on the identification label or displayed by the mobile forensic software does not match. These discrepancies can lead to problems when documenting and even testifying to the identity of the device if not clearly understood.
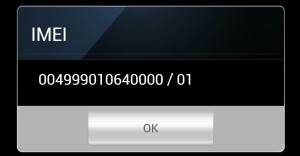
For both the IMEI AND IMEISV The most important numbers are the first 8 and the next 6 (TAC and Serial Number). The numbers following will either be the check digit (with a 0 filler to reach 15 digits) or the software version composed of two digits. What should also be known is that the two software digits can change over time based upon an update to the device’s software. With today’s devices this can be a frequent occurrence! With Android devices pressing the common *#06# will list the IMEISV in the form of 17 digits (TTTTTTTT-NNNNNN-C / SS) whereas iOS devices will simply display the common 15 (TTTTTTTT-NNNNNN-C). However, both CDR data from carriers and mobile forensic software often only list the standard IMEI number while others list the IMEISV. At times some mobile forensic software lists both!
As long as the examiner understands that the significant numbers within the IMEI or IMEISV are the first 8 and following 6 clarity can easily be demonstrated and described when requested to do so.
By knowing:
- the exact IMEI that is listed on the identification label can be derived from the IMEISV to show unequivocally they are the same,
- that the multiple IMEIs listed by the forensic tool are just the IMEI and IMEISV,
- and the returned IMEI from a telco that is off by a few digits is the IMEISV not the anticipated IMEI, you can make an informed analysis and conclusion.
More tips and information can be found in my book, Mobile Forensic Investigations: A Guide to Evidence Collection, Analysis, and Presentation
Good Luck!


 er all of the requests to dump my brain into a book I finally listened producing MobileForensics Investigation: A Guide to Evidence Collection, Analysis, and Presentation. It is currently in most book outlets and also
er all of the requests to dump my brain into a book I finally listened producing MobileForensics Investigation: A Guide to Evidence Collection, Analysis, and Presentation. It is currently in most book outlets and also 