In the beginning there was a bit. The bit turned into a byte. That byte rapidly turned into a kilo. The kilo turned into a mega, the mega into a giga, and the giga into what we know today as a tera. Sounds like an interesting name game, but truthfully each name means extra time to the forensic examiner, extra data, and most of the time, extra headaches. As a digital examiner, I saw firsthand how the progression of large data sets in digital investigations put a damper on both information collection, as well as the investigator. The first examination of a floppy disk could be turned around in a day. A 500MB drive required a week turn around. A large gigabyte drive took multiple weeks, and larger data sets require longer processing times . Since the amount of cases involving Big Data did not stop I began to see backlogs stack up, causing frustration in many of the people requesting the examinations. We dealt with this problem by changing the way we conducted examinations, not by short-cutting the forensic process, but by focusing just on the information requested.
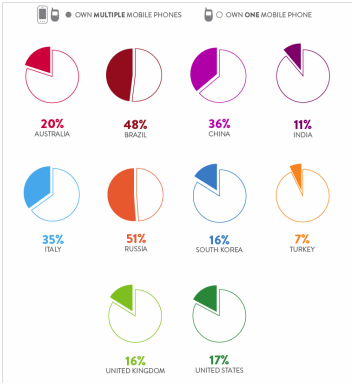
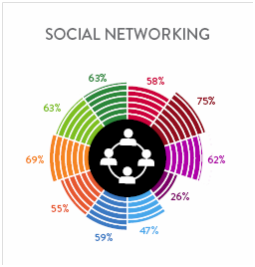
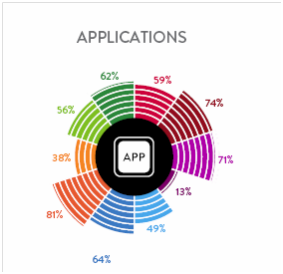
Mobile devices hit the scene requests for information began to pour in, and the same progression was seen. The mobile devices which contained only 10 kb of data were collected to yield the requested data of contacts, call logs, SMS, and media in a matter of minutes. The people requesting the data were so excited about this new technology that the requests for this data soon outnumbered requests for computer examinations. Grab the phone, dump the data, and create the report in 5 minutes or less. Since the requests began to pile up, doing 10 phones a day was not uncommon and those requesting the work soon grew tired of waiting in line, so the examination of mobile devices moved away from the lab and into the field. This shift is the most significant difference between a computer forensic examiner and a mobile device examiner. The problem with this shift is that the time taken to examine a 10 KB mobile device and a 64 GB iPhone is no different. Granted, the time to collect the data might be from 5 minutes to now 20 minutes but the outcome is the same, surface data. Agencies are now saving time and allowing the person in the field to conduct the collection and field triage. As you notice I did not say examination because most tools that extracted the first mobile devices give the same output as they do with the 64GB device. This is simply because the field only wants actionable intelligence and has grown accustomed to only getting that “tip of the iceberg” data. What is not yet obvious is that this does not have to be the case. Wouldn’t it be beneficial to extract all data, give a report of actionable intelligence and allow the examination of additional data at a later time? A detailed examination that can be conducted by investigator training in digital evidence that might have the time to look for that needle in the haystack? Using Mobile Phone Examiner Plus nFIELD™ (MPE+ nFIELD™) can do that.
MPE+ nFIELD allows the logical and physical collection of mobile devices with little training, little knowledge or experience. Select the item you will be collecting (Figure 1.) Select the items to extract (Figure 2.) and the data and report is then available at the saved location (Figure 3). The most important feature comes in the form of data integrity. All the collected data is then saved into an AD1 file. This AD1 file is an evidence locker that will allow the collected data to not only stand up in court, but will allow the information to be further analyzed in the full feature MPE+. The person collecting the data on-scene gets their report immediately to gain actionable intelligence while the integrity of the evidence is not compromised and a full exam is still possible.
TIME is very valuable in the age of digital device examinations, but obtaining critical data and allowing for full examinations if needed is mandatory. We all understand that mobile device examinations are becoming more and more important to any investigation, but we also recognize that the data recovered must survive the scrutiny of the court. AccessData responds to both challenges with the new MPE+ nFIELD solution.